Your company’s data is the backbone of your organization’s decision-making and maintaining its security and protection should always be a top priority. As organizations migrate to and rely increasingly on modern, cloud-hosted data platforms for analytics and decision-making, the risk of data breachesᅳspecifically data exfiltrationᅳcontinues to grow. Data exfiltration, which is the unauthorized transfer of data out of your environment, poses a critical threat that can lead to devastating financial and reputational damage. According to a market survey, the global Data Exfiltration size is projected to reach about US $716.6 billion by 2030. To combat this, building a zero trust network architecture is essential in ensuring that your environment remains secure from unauthorized access and data loss. In this post, we’ll explore how strengthening your network architecture plays a crucial role in safeguarding your Databricks environment.
What is Data Exfiltration?
At its core, data exfiltration is the process of data being taken out of a secure environment without authorization. This can be due to malicious intent, misconfiguration, or lack of oversight. Simply put, it is a form of data theft. Organizations can significantly minimize the risk of data exfiltration by designing a security-enforced network. In addition to the robust controls Databricks provides within the platform organizations need to evaluate data exfiltration risk by designing a security-enforced network.
Optimize Security and Scalability with a Hub-and-Spoke Network Architecture for Databricks
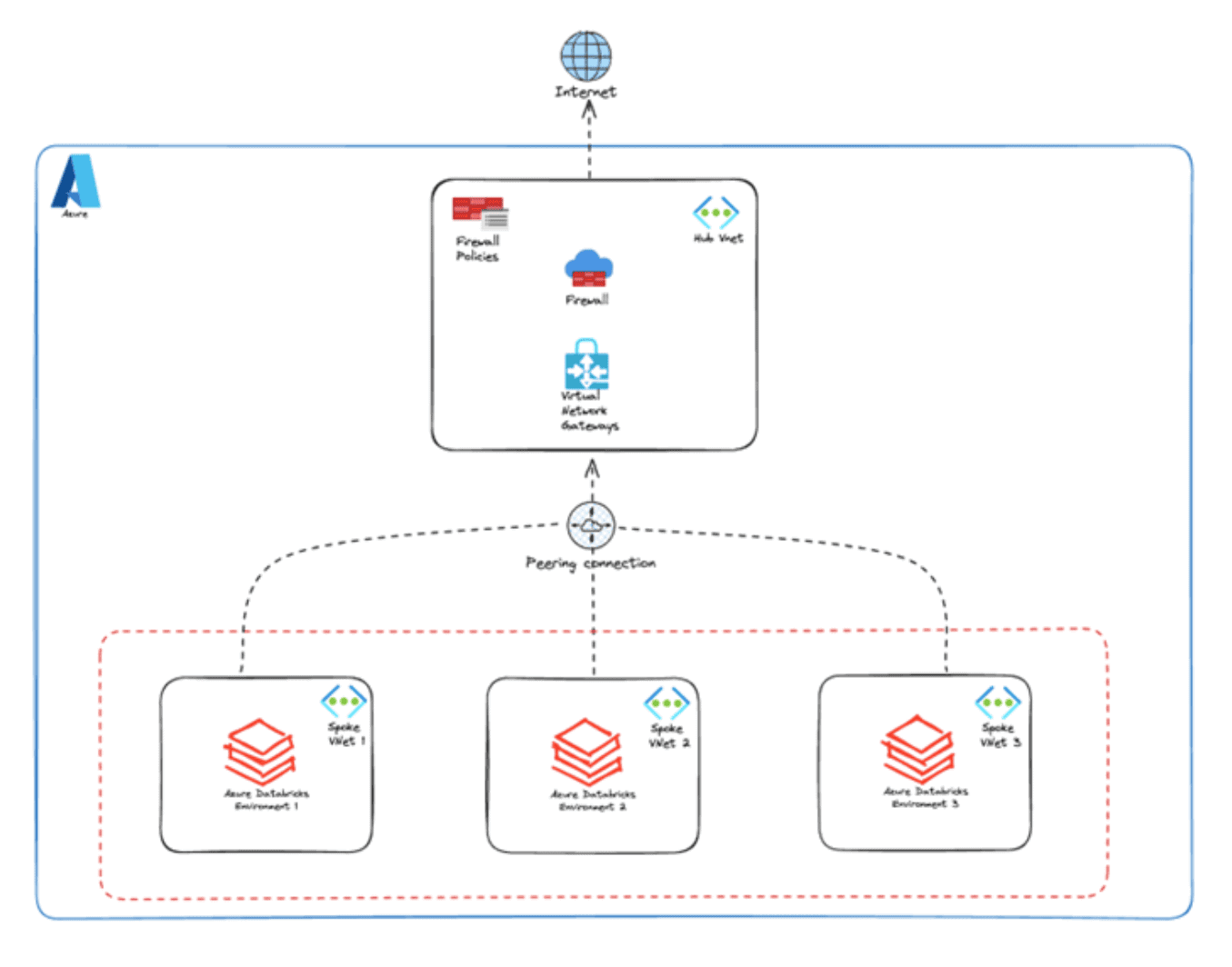
Lovelytics recommends a hub-and-spoke network that provides a scalable way to centralize network security while maintaining isolation. To describe this topology for an Azure Databricks environment, the hub VNet acts as a central point where shared services such as firewalls and monitoring services reside. The spoke VNets, which peer with the hub, house specific workloads such as various Databricks environments. This design allows tight and secure control between all services and adequate monitoring via the hub VNet, where strict network rules can be enforced.
Centralized Security allows the deployment and management of network security resources in the hub and filters all ongoing traffic. This also ensures that all egress traffic from resources like Databricks Clusters are routed through the firewall ensuring that all sensitive data is protected at all times.
Isolation and Segmentation of platforms such as Databricks in a dedicated spoke VNet ensures communication with only approved services reducing the risk of unauthorized access.
Some key benefits of the hub-and-spoke network design include:
- Enhanced Security and Compliance: Centralizing security within the hub ensures that all data traffic is monitored, filtered, and controlled through a single point, reducing the risk of breaches and enhancing compliance with regulatory standards. Organizations can efficiently safeguard sensitive data, ensuring end-to-end protection across environments.
- Scalability and Flexibility: The hub-and-spoke design supports easy scalability, enabling organizations to add new workloads or environments (such as additional Databricks clusters) without the need for complex reconfigurations. This helps businesses expand their operations and data capacity while maintaining the same level of security and control.
- Operational Efficiency: With centralized security and monitoring, the overall complexity of managing network infrastructure is significantly reduced. By simplifying operations, IT teams can focus on more strategic tasks, freeing up resources to innovate and enhance service delivery without compromising network performance or security.
- Cost Optimization: By consolidating shared services like firewalls and security monitoring within the hub, organizations can avoid duplicating security resources across different environments, leading to cost savings. Additionally, the streamlined network management reduces the need for extensive IT overhead, further contributing to cost efficiency.
Overall, this architecture not only ensures robust security but also empowers organizations to grow, innovate, and manage resources effectively, positioning them for long-term success. This is what a high-level overview looks like:
By centralizing critical security services like firewalls and monitoring within the hub, this design simplifies the management of environments while enhancing security and compliance across the organization.
Lovelytics has applied its security-first approach to help organizations implement scalable, secure data platforms that protect against unauthorized data transfers.
Securing Data with Confidence: A Scalable and Safe Platform for a Global Investment Firm
Lovelytics partnered with a global investment banking and advisory firm to build a scalable and secure data platform that empowered its data science teams to process data efficiently while safeguarding against unauthorized data transfers. Given the sensitive nature of the data, preventing data exfiltration was a top priority for the firm’s security team.
To address these needs, Lovelytics implemented a comprehensive hub-and-spoke network architecture featuring:
- Hub and Spoke Network Design
- Azure Privatelink
- Azure Firewall for Egress Control
- Networks Security Groups
- Comprehensive Monitoring and Alerts
This solution’s robust network architecture enabled the firm to successfully leverage Databricks to drive key business insights while ensuring the security of sensitive customer data. The implemented solution not only reduced the risk of data exfiltration but also enhanced compliance, customer trust, and operational efficiency.
As organizations increasingly rely on Databricks for advanced analytics, securing data against unauthorized access is paramount. Lovelytics’ security-first approach, utilizing a robust hub-and-spoke network architecture, provides a scalable solution that enhances data protection, operational efficiency, and compliance. By centralizing security controls and monitoring, this architecture enables businesses to innovate confidently, ensuring sensitive data is secure while maintaining optimal performance. Our collaboration with leading organizations highlights the power of this approach in safeguarding data and driving business insights.
Ready to secure your data with confidence? Partner with Lovelytics to bring unparalleled security, efficiency, and compliance to your Databricks environment. Discover how our hub-and-spoke architecture can safeguard your most valuable insights.